Видео с ютуба Rsa Vulnerabilities

Breaking RSA - Computerphile

Some Attacks Against RSA

ECED4406 0x20A - RSA Attacks

Attacking RSA with lattice reduction techniques (LLL)
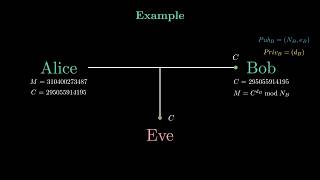
The RSA Encryption Algorithm - How Does It Actually Work + Step-by-Step Example.

The RSA Encryption Algorithm (1 of 2: Computing an Example)

Bleichenbacher Attack on RSA PKCS #1 v1.5 For Encryption

AI Security Engineering—Modeling/Detecting/Mitigating New Vulnerabilities

Anatomy of the RSA targeted attack

RSA

The Encryption That Runs The Internet | RSA Encryption

Prime Numbers & RSA Encryption Algorithm - Computerphile

How RSA Works

Attacks on RSA || Lesson 61 || Cryptography || Learning Monkey ||

Breaking RSA Encryption - TryHackMe

Attacks on RSA Signature || Lesson 88 || Cryptography || Learning Monkey ||

RSA Algorithm - How does it work? - I'll PROVE it with an Example! -- Cryptography - Practical TLS

The Power of Vulnerability - Brene Brown

RSA Security: Honest Review & User Experience of RSA's Cybersecurity Solutions

Quantum Researchers Break RSA Encryption